系统安全(Security)
Security即用CD(Live-CD)
Live-CDIf you start Puppy from CD-ROM (or from a CD-image on your harddrive) no potentially harmful programs can install on your computer. With every reboot all potential malware is gone.
However you are not wholly protected against malware while you are online, because (in theory) malware can be installed on your computer and can be active until the next reboot. That is why you should always run a firewall. Besides you can store checksums of all your files to make sure, no one has manipulated your files.
超级用户(Root)
RootIn contrast to most other Linux distributions Puppy does not differentiate between a normal user and the administrator root. Rather you always works as root, which simplifies the use of Puppy. The question arises if it is unsecure to work as root and to have full access to all files, programs and data.
For the normal home user, there are no special risks compared to other Linux distributions. On the contrary, Puppy is probably a bit safer than many other distributions.
First let's analyze the risk of a distribution, which differentiates between user and root. The user works as a normal user, who does not have privileges to write/delete programs and system files. An intruder can compromise only the user’s files. However the intruder has an entrance to the system and can try to gain root-privileges (find the password file, use exploits to transfer malware code and so on), and afterwards try to get access to all files.
As long as Puppy starts from CD-ROM (and is not installed on the harddrive) the program-files and system-files are secure. Everytime you reboot any malware programs, which an intruder could have left, are gone. Of course your own files stored into the pup_save.3fs-file or on a harddrive can be compromised by an intruder, but this can happen to the normal user of another Linux-distribution as well. If you want to be safe from intrusion, store checksums of all files and backup your files regulary.
防火墙与守护进程(Firewall and daemons)
Firewall and daemonsYou should always have an active firewall. It allows you to controlwhat ports your PC uses to communicate with the Internet. Ideally, allports are closed.
Start "Menu | Setup | Linux-Firewall Wizard".

Go to the "default" entry using the Arrow Down key (this option closes all ports) and press Return.
Now you can check the firewall rules. Confirm the default ("Yes") with the Return key.
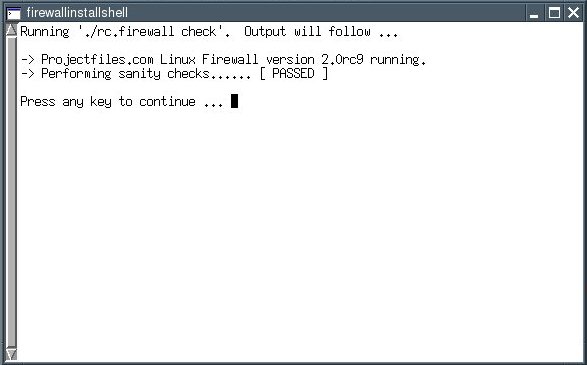
The line that reads "Performing sanity checks ..." should display "PASSED" now. Press the key you love best ...
... to get to the next dialogue. It allows you to activate the firewall rules.
Confirm the default ("Yes") with the Return key.

The firewall is now active. Hit Return to finish setup.
The "default" option you selected closes all ports. You can specifywhich ports should be left open using the Firewall Wizard's "custom"option. You should only open the ports you really need. If you use acertain port only occasionally, you should open it only when you needit. An open port is usually not a security risk per se. It only becomesvulnerable if your PC is running a service (a so-called "daemon") whichuses that port to listen for incoming requests. This is why you shouldnot run any daemons you do not need on your PC.
This is how to check for which ports are open and which services are running:
Install the Program nmap. Nmap is available as a PETget.
Open a shell and enter:
nmap localhost
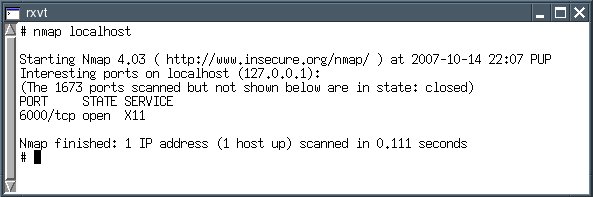
This lists open ports. A home user without a home network of her ownshould have no open ports. The X11 service is open because it is theone responsible for the graphical desktop.
The following command gives you a list of which services are listening on which ports:
netstat -anp --ip
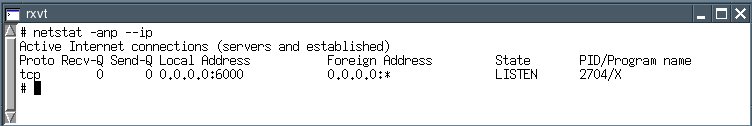
This list, too, should be empty except for the X11 port if you are ahome user who does not run a web server or a home network; i.e., noservices (daemons) should be running.
You can test your firewall at the Web site Shields Up!. Load the page and click the Proceed-button.
病毒查杀(Virus scanner)
Virus scannerIf you want to scan your files or a Windows computer you can use F-Prot virus scanner. You can download the program from the Forum. After you have downloaded and installed the program open a shell and enter the following command while you are still online.
/usr/local/bin/xfprot-gtk
or
/usr/local/xfprot/xfprot-gtk
Now you can update the virus definitions. Then you can get offline.Mount your Windows-partition (mount /dev/hdax /mnt/hdax) and make thefollwing settings in F-Prot:
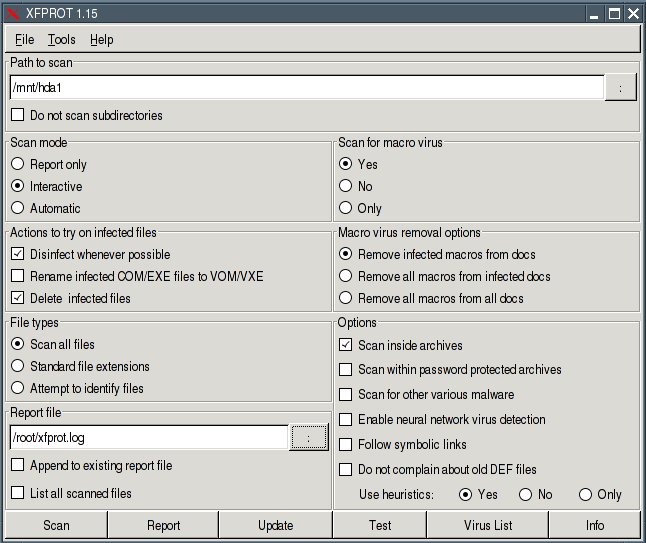
Path to scan: /mnt/hdax
Scan mode: Interactive
Report file: /root/xfprot.log
When the virus scan has finished you can find the log-file at /root/xfprot.log.
If you want to scan another Windows computer, you can remasterPuppy. Boot the Windows computer from the remastered Puppy CD(boot-option puppy pfix=ram) and scan the PC as described above.
入侵检测(Intrusion detection)
Intrusion detectionFor further improvement of your security you should store a checksum (a fingerprint) for all files. At regular intervals, but in any case before a backup, you examine the checksums of your files. If the checksums do not agree, the file was changed or deleted.
In order to compute and store the checksums, you open a shell and enter the following commands:
md5sum /usr/bin/md5sum
Create a checksum of the program md5sum. Write down the checksum.
mount /dev/hda4 /mnt/hda4
Mount the harddrive with your files.
find /mnt/hda4 -type f -exec ls -ail {} \; \-exec md5sum {} \; > /root/check1.dat
Create the file check1.dat with the checksums of all files.
md5sum /root/check1.dat
Create a checksum of the file. Write down the checksum.
If you want to check, which files have been changed enter these commands:
md5sum /usr/bin/md5sum
Create a checksum of the program md5sum. Compare the checksum with the checksum of step (1).
md5sum /root/check1.dat
Create a checksum of the file /root/check1.dat. Compare the checksum with the checksum of step (3).
mount /dev/hda4 /mnt/hda4
Mount the harddrive with your files.
find /mnt/hda4 -type f -exec ls -ail {} \; \-exec md5sum {} \; > /root/check2.dat
Create the file check2.dat with the actual checksums of the files.
diff /root/check1.dat /root/check2.dat > /root/diff.txt
Compare the two files check1.dat and check2.dat. The differences are written to the file diff.txt.
Open the file /root/diff.txt and check, if you know about the changed files. If not think why these files have been changed.
Delete the file /root/check1.dat
Rename the file /root/check2.dat as /root/check1.dat.
md5sum /root/check1.dat
Create a checksum of the new check1.dat-file. Write down the checksum.
用bcrypt加密文件(Encrypt with bcrypt)
Encrypt with bcryptYou should encrypt very sensitive files with the program bcrypt. Bcrypt uses the secure Blowfish-algorithm.
Open a shell and enter:
bcrypt /MyDirectory/MyFile
Then you are asked a passwort (at least eight characters long; you can abort bcrypt with "Ctrl" + "C"). Bcrypt encrypts your file and appends the extension bfe to the file. The original file is deleted automatically.
If you want to encrypt more than one file or a complete directory you should create an archive-file. Start the program "Menu | Utilities | Xarchive archiver". Afterwards you encrypt the archive-file.
Note that bcrypt deletes the original file automatically. You can't recover the file. If you don't want to delete the file start bcrypt with the option -r:
bcrypt -r /MyDirectory/MyFile
If you want to decrypt the file start bcrypt again:
bcrypt /MyDirectory/MyEncryptedFile
Than you enter your password.
For further information see :
Homepage bcrypt